-
What Grafana version and what operating system are you using?
helm version 6.34.0 and grafana version 9.1.1
OS: linux ubuntu. Grafana on k8s cluster. helm version: v3.5.2 -
What are you trying to achieve?
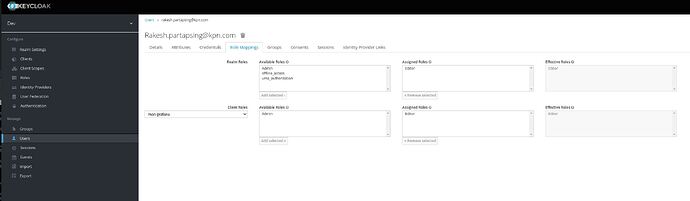
Enable the Editor or Admin role via keycloak. -
How are you trying to achieve it?
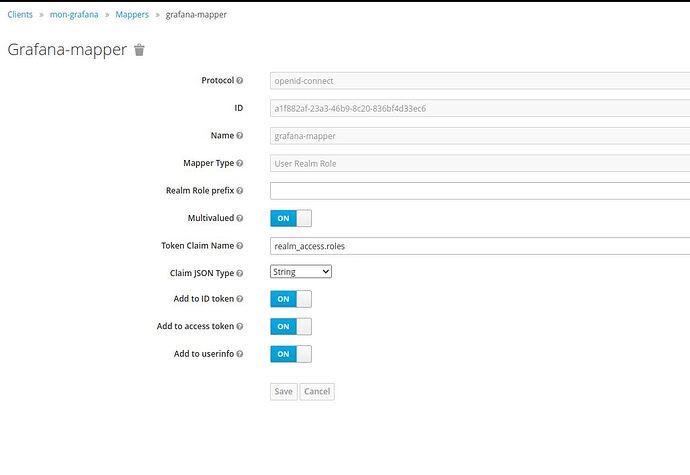
Creating a client, role and mapper in keycloak
Creating a user and assigning the role to the user
enablingrole_attribute_path: "contains(roles[*], 'admin') && 'Admin' || contains(roles[*], 'editor') && 'Editor' || 'Viewer'" -
What happened?
My role is still the default: Viewer
❯ curl -XGET -H "Content-Type: application/json" -u "admin:<my_pw>" http://localhost:3002/api/access-control/status
{"message":"Not found"}
❯ curl -XGET -H "Content-Type: application/json" -u "admin:<my_pw>" http://localhost:3002/api/access-control/roles
{"message":"Not found"}
-
What did you expect to happen?
I should have obtained the role of Editor -
Can you copy/paste the configuration(s) that you are having problems with?
/usr/share/grafana $ cat /etc/grafana/grafana.ini
[analytics]
check_for_updates = true
[auth]
disable_login_form = true
oauth_auto_login = true
signout_redirect_url = https://auth.dev.test-cp.kpn-dsh.com/auth/realms/Dev/protocol/openid-connect/logout?redirect_uri=https://monitoring.test-cp.kpn-dsh.com/login
[auth.generic_oauth]
allow_sign_up = true
api_url = https://auth.dev.test-cp.kpn-dsh.com/auth/realms/Dev/protocol/openid-connect/userinfo
auth_url = https://auth.dev.test-cp.kpn-dsh.com/auth/realms/Dev/protocol/openid-connect/auth
client_id = mon-grafana
client_secret = 480171f4-ae55-43df-b480-c442be62a8aa
enabled = true
login_attribute_path = preferred_username
name = OAuth login
role_attribute_path = contains(roles[*], 'admin') && 'Admin' || contains(roles[*], 'editor') && 'Editor' || 'Viewer' || contains(roles[*], 'sre-editor')
scopes = openid user email
tls_skip_verify_insecure = False
token_url = https://auth.dev.test-cp.kpn-dsh.com/auth/realms/Dev/protocol/openid-connect/token
[grafana_net]
url = https://grafana.net
[log]
level = debug
mode = console
[paths]
data = /var/lib/grafana/
logs = /var/log/grafana
plugins = /var/lib/grafana/plugins
provisioning = /etc/grafana/provisioning
[plugins]
allow_loading_unsigned_plugins = camptocamp-prometheus-alertmanager-datasource
[server]
domain = monitoring.test-cp.kpn-dsh.com
root_url = https://%(domain)s/
[smtp]
enabled = true
from_address = monitoring-dsh-notifications@kpn.com
from_name = DSH monitoring
host = safemail.kpnxchange.com:25
skip_verify = True
- Did you receive any errors in the Grafana UI or in related logs? If so, please tell us exactly what they were.
no errors were given also not in debug mode
- Did you follow any online instructions? If so, what is the URL?
https://community.grafana.com/t/roles-not-being-assigned-with-integration-with-keycloak-for-oauth/51723
Hi Guys,
So what I need is to assign the editor role to us Site Reliability Engineers through keycloak.
Login in through keycloak works as expected but the roles are not propagated into grafana.
Please let me know what I am missing here. I guess my mapper is not correct?